5 Essential UCaaS Security Best Practices
Unified communications as a service (UCaaS) platforms have become lifelines for businesses, enabling seamless collaboration and flexibility. However, this convenience also comes with challenges. Cybercriminals are constantly searching for vulnerabilities in voice, video, messaging, and file-sharing apps, making it crucial for organizations to stay one step ahead.
The World Economic Forum’s Global Cybersecurity Outlook 2025 revealed that 72% of organizations experienced more cyber risks last year,1 underscoring the critical need for stronger security. A few of the most pressing security challenges facing businesses include:
- Phishing and Social Engineering Attacks: Cybercriminals often impersonate trusted contacts to gain unauthorized access to UCaaS platforms, leading to data theft or account compromise.
- Data Breaches: Cloud-based communication systems store sensitive data that can become a target for hackers if not properly secured.
- VoIP and Call Interception: Without encryption and secure authentication, cybercriminals can intercept VoIP calls, leading to potential data leaks or fraud.
- DDoS Attacks: Distributed Denial-of-Service (DDoS) attacks can overwhelm UCaaS infrastructure, disrupting business operations and preventing legitimate users from accessing services.
As UCaaS adoption grows, so do the risks associated with cloud-based communication. Read on to explore the top UCaaS security best practices to safeguard your business communications from today’s threats.

Top 5 UCaaS Security Best Practices
Protect your digital communication infrastructure with these best practices:
1. Implement Strong Authentication Measures
Multi-factor authentication (MFA) goes beyond traditional password protection by requiring two or more forms of verification before providing access. Role-based access control (RBAC) is another important measure, as it limits permissions to ensure users only have access to the resources they need for their specific job.
2. Encrypt All Communications
Encryption converts your company’s conversations into unreadable code to thwart potential interceptors and ensure sensitive business communications remain confidential. Secure SIP trunking and TLS-based encryption for VoIP traffic also improve security by protecting your voice infrastructure from eavesdropping and data interception – so even if unauthorized parties gain access to communication channels, they can’t decipher the actual content of the conversations.
3. Monitor and Audit User Activity
Real-time monitoring systems let your IT teams detect suspicious behaviors and potential security breaches by identifying unusual login patterns, unexpected access attempts, and other potential indicators of compromise. Security audits complement this approach, providing a comprehensive assessment of your organization’s existing vulnerabilities and ensuring security policies remain effective and up-to-date.
4. Protect Against Phishing Attacks
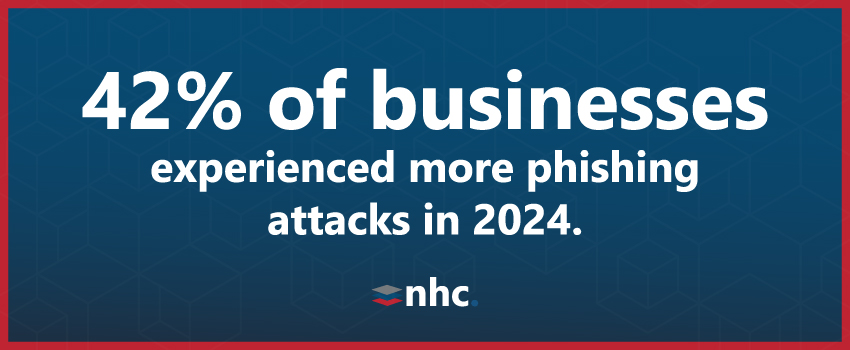
Social engineering threats rose in 2024, with 42% of businesses reporting an increase in phishing attacks.1 Providing your staff with cyber security awareness training helps them recognize and respond to phishing attempts effectively, so it’s important to develop ongoing education programs that keep employees informed about the latest social engineering tactics.
AI-powered threat detection technologies also help protect against these risks. They use smart machine learning algorithms to identify and block suspicious logins and potentially fraudulent communications.
5. Secure Hybrid Work Environments
The modern workplace demands flexible yet secure communication solutions. Implementing VPNs or zero-trust architecture can help your teams connect safely and securely, no matter where they’re accessing your network from. Endpoint security solutions are also important here, as they ensure every device connecting to your UCaaS platform meets strict security standards.
Strengthen Your UCaaS Security With NHC
At NHC, we prioritize UCaaS security best practices to help businesses and partners deliver secure, scalable communication solutions. Our UCaaS services combine every channel your teams need to connect into one easy-to-manage platform – and simplify delivery via our secure cloud network.
If you’re looking for a trusted UCaaS provider that delivers both functionality and security, contact the NHC team today.
Sources:



